EFF’s Updated List Of Who Protects Your Online Information
This article, compiled by senior staff attorney Kurt Opsahl, staff attorney Nate Cardozo and activist Parker Higgins, was originally published by the Electronic Frontier Foundation on Dec. 5.
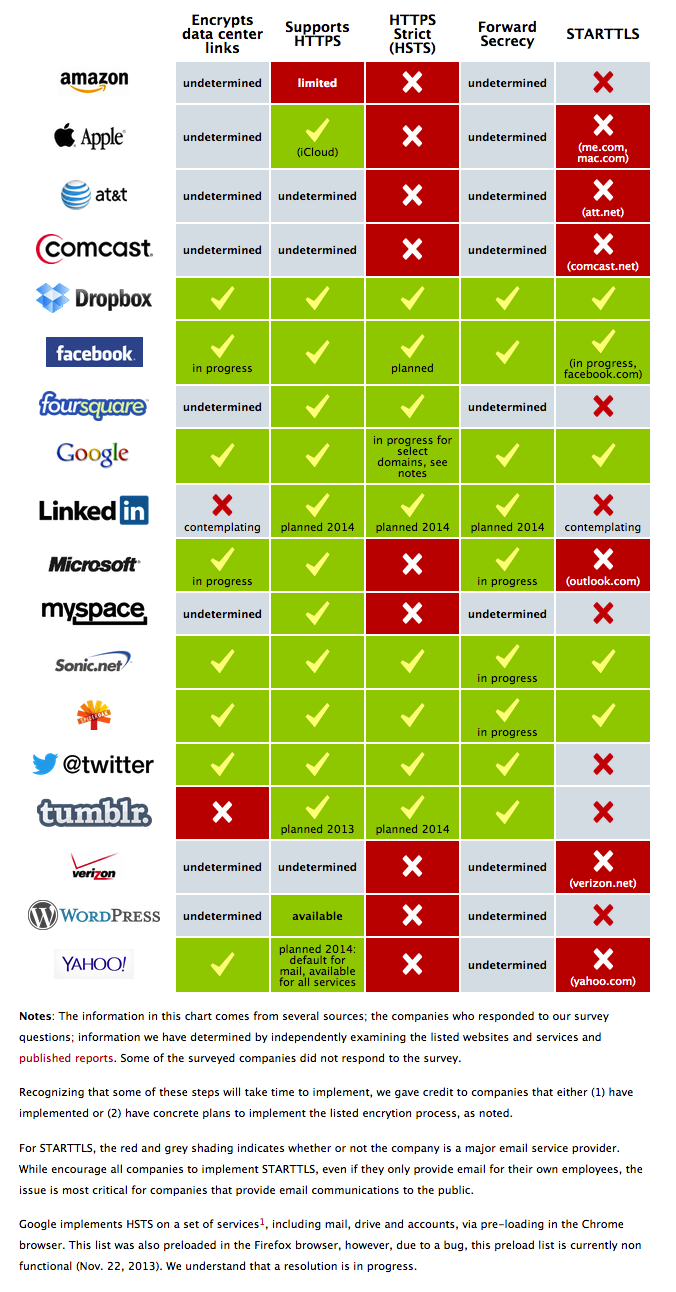
The Electronic Frontier Foundation has asked the companies in its Who Has Your Back Program what they are doing to bolster encryption in light of the National Security Agency’s unlawful surveillance of your communications. EFF is pleased to see that four companies — Dropbox, Google, SpiderOak and Sonic.net — are implementing five out of five of EFF’s best practices for encryption. In addition, EFF appreciates that Yahoo! just announced several measures it plans to take to increase encryption, including the very critical encryption of data center links, and that Twitter has confirmed that it has encryption of data center links in progress. See the infographic.
By adopting these practices, described below, these service providers have taken a critical step toward protecting their users from warrantless seizure of their information off of fiber-optic cables. By enabling encryption across their networks, service providers can make backdoor surveillance more challenging, requiring the government to go to courts and use legal process. While Lavabit’s travails have shown how difficult that can be for service providers, at least there was the opportunity to fight back in court.
While not every company in EFF’s survey has implemented every recommendation, each step taken helps; and EFF appreciates those who have worked to strengthen their security. EFF hopes that every online service provider adopts these best practices and continues to work to protect their networks and their users.
Crypto Survey Results
UPDATE, Nov. 20: Facebook and Tumblr have provided further information to supplement the Encrypt the Web Report. EFF is pleased to report that Tumblr is planning to upgrade its Web connections to HTTPS this year and implement HSTS by 2014, and Facebook is working on encrypting data center links and implementing STARTTLS.
UPDATE, Nov. 22: Google has provided further information to supplement the report on its use of HSTS. See the updated chart below and the notes for more information.
UPDATE, Dec. 5: Microsoft has provided further information, announcing a plan to expand encryption across all its services, including encrypting links between data center and implementing forward secrecy by the end of 2014.
Why Crypto Is So Important
The NSA’s MUSCULAR program, which tapped into the fiber-optic lines connecting the data centers of Internet giants like Google and Yahoo, exposed the tremendous vulnerabilities companies can face when up against as powerful an agency as the NSA. Bypassing the companies’ legal departments, the program grabbed extralegal access to your communications, without even the courtesy of an order from the secret rubber-stamp Foreign Intelligence Surveillance Court. The program is not right, and it’s not just.
With that in mind, EFF has asked service providers to implement strong encryption. EFF would like to see encryption on every step of the way for a communication on its way to, or within, a service provider’s systems.
For starters, EFF has asked companies to encrypt their websites with Hypertext Transfer Protocol Secure (HTTPS) by default. This means that when a user connects to a website, it will automatically use a channel that encrypts the communications from the user’s computer to the website.
EFF has also asked them to flag all authentication cookies as secure. This means cookie communications are limited to encrypted transmission, which directs Web browsers to use these cookies only through an encrypted connection. That stops network operators from stealing (or even logging) users’ identities by sniffing authentication cookies going over insecure connections.
To ensure that the communication remains secure, EFF has asked companies to enable HTTP Strict Transport Security (HSTS). HSTS essentially insists on using secure communications, preventing certain attacks where a network pretends that the site has asked to communicate insecurely.
All of these technologies are now industry-standard best practices. While they encrypt the communications from the end user to the server and back, the MUSCULAR revelations have shown this is not enough. Accordingly, EFF has asked service providers to encrypt communications between company cloud servers and data centers. Anytime a user’s data transits a network, it should be strongly encrypted, in case an attacker has access to the physical data links or has compromised the network equipment.
In addition, we have asked for email service providers to implement STARTTLS for email transfer. STARTTLS is an opportunistic encryption system, which encrypts communications between email servers that use the Simple Mail Transfer Protocol (SMTP) standard. When a user emails someone on a different provider (say, a Hotmail user writing to a Gmail user), the mail message will have to be delivered over the Internet. If both email servers understand STARTTLS, then the communications will be encrypted in transit. If only Gmail does but Hotmail does not (the current situation), they will be in the clear and exposed to eavesdropping, so it’s critical to get as many email service providers as possible to implement the system.
Finally, EFF has asked companies to use forward secrecy for their encryption keys. Forward secrecy, sometimes called “perfect forward secrecy,” is designed to protect previously encrypted communications, even if one of the service providers’ keys is later compromised. Without forward secrecy, an attacker who learns a service provider’s secret key can use it to go back and read previously incomprehensible encrypted communications — perhaps ones that were recorded months or years in the past.
- 1. The HSTS domains are wallet.google.com; checkout.google.com; chrome.google.com; docs.google.com; sites.google.com; spreadsheets.google.com; appengine.google.com; encrypted.google.com; accounts.google.com; profiles.google.com; mail.google.com; talkgadget.google.com; talk.google.com; hostedtalkgadget.google.com; plus.google.com; plus.sandbox.google.com; script.google.com; history.google.com; security.google.com; goto.google.com; market.android.com; ssl.google-analytics.com; drive.google.com; googleplex.com; groups.google.com; apis.google.com; chromiumcodereview.appspot.com; chrome-devtools-frontend.appspot.com; codereview.appspot.com; codereview.chromium.org; code.google.com; dl.google.com; translate.googleapis.com; oraprodsso.corp.google.com; oraprodmv.corp.google.com; gmail.com; googlemail.com; www.gmail.com; www.googlemail.com; google-analytics.com; and googlegroups.com.
No comments:
Post a Comment
Thanks for commenting. Your comments are needed for helping to improve the discussion.